IT Security: Wireless Dictionary Attack
Posted on: October 12, 2025
This week, I'd like to continue on from my last article, IT Security: Wireless Deauthentication. After demonstrating deauthentication to my cybersecurity students, I like to follow up with the logical next step: performing a dictionary attack to crack a wireless network password. In this article, we'll cover what a dictionary attack is, how these attacks work, and how to defend against them. We'll wrap up with a demonstration of a simple dictionary attack in action.
What is a Dictionary Attack?
A dictionary attack is a way of cracking a password by cycling through a pre-defined list of values, attempting each one until the correct one is found. Think of it as automated password guessing. The pre-defined list of values, or dictionary, may be a simple text file with a potential password per line that is inserted into a command, script, or program. These dictionaries can be created or found online. If you search for password lists, you will find plenty of sources through GitHub, PasteBin, etc. with readily available dictionary files that are thousands, millions, tens of millions of values long. In these files you'll find literal dictionary words, often alongside passwords from known breaches. Keep in mind that the longer the list, the more time the attack will take to complete.
You may be familiar with a brute force or rainbow table attack and may wonder what the difference is. A brute force attack tries every possible character combination. No list is inserted into the process. A rainbow table attack attempts to crack the hash of a password. Rather than making an attempt with a plaintext password, a precalculated hash value is compared against the stored password at the target device or domain. This is similar in that a dictionary attack must compute the hash values of every guess as part of its process if the target stores the hashed value. Rainbow table attacks remove the need for that, increasing efficiency and reducing the time it takes to cycle through the same amount of values.
Cracking Wireless
Now that we know what a dictionary attack is and the gist of how it works, how does that apply to cracking a Wi-Fi password? First, we need to capture a 4-way handshake. One way of forcing this - which is why this is a continuation of my deauthentication demonstration - is to deauthenticate a client device that is connected to our target network. If the client is set to automatically rejoin the network, it will drop from the network and then immediately reauthenticate and initiate a 4-way handshake. Note that deauthentication isn't necessarily required; if a client connects naturally while you're monitoring, you can capture a handshake passively.
The information captured in the 4-way handshake makes password guessing possible. Altogether you get the Authenticator Nonce (ANonce), a random number generated by the AP, the Supplicant Nonce (SNonce), a random number generated by the client, the MAC addresses of both the access point (AP) and the client, the Message Integrity Code (MIC), which verifies the integrity of the handshake messages, and the Encrypted EAP-Over-LAN (EAPOL) frames which carry Extensible Authentication Protocol (EAP) messages across the network. Using this information, we need to determine the Pairwise Master Key (PMK) and the Pairwise Transient Key (PTK). The PMK is generated by running the pre-shared key (PSK) against the PBKDF2 algorithm with SHA-1. The PTK is derived from the PMK, the ANonce, the SNonce, and the MAC addresses from both the client and the AP during the 4-way handshake and is used to encrypt the data being transmitted between the client and the AP.
How does this information enable a dictionary attack against a wireless network? The attacker's goal is to reproduce the MIC. Once a PTK is generated, it is split into components. One of these components, the Key Confirmation Key (KCK), is used to generate the MIC. When an attacker tries a potential password, the tool in use creates a PMK from the potential password, then it generates a PTK using the information captured from the handshake, generates a KCK, and finally generates a MIC to compare against the MIC in the capture. If the MICs match, we have our password. Otherwise, loop to the next potential password in the dictionary file.
Prevention
Preventing a dictionary attack begins with everyone's favorite: strong password practices. Using a strong, 16+ character password that uses numbers and special characters is ideal when your network is protected by a PSK. Avoiding dictionary words is also recommended. Recycling the password periodically is a good idea. Using enterprise-grade WPA-2 or WPA-3 can also help mitigate these attacks, assuming you have a RADIUS server in your network. WPA-3 also has a resistance to offline dictionary attacks thanks to the Simultaneous Authentication of Equals (SAE) protocol, which prevents attackers from capturing handshakes. Many of the recommendations in the deauthentication article also stand here as these attacks can begin with deauthentication.
Demonstration
DISCLAIMER:
I am going to walk through using aircrack-ng to crack a WPA2 wireless network's password. This is purely for educational purposes. I own every piece of this lab environment: the virtual machines, the wireless access point and network, everything. DO NOT perform any of this on equipment or networks you do not personally own.
Lab Details:
This demo will utilize a Kali VM, an Alfa AWUS036NH USB wireless adapter that is passed through to our Kali VM, and one Ubiquiti Unifi U6 Pro WAP. There are many combinations of equipment that will work, you won't necessarily need this exact setup to successfully complete the following steps. The most important part will be making sure the wireless adapter you get supports monitoring and injection; Not all adapters do. This lab is on its own VLAN, isolated from my other networks. We will be interested in the LabWiFi wireless network.
There are several tools out there that can perform a dictionary attack: John the Ripper, aircrack-ng, Hydra, Hashcat. For this demonstration we will be using aircrack-ng from our Kali terminal. We'll also assume we already know the BSSID of our target network and skip deauthentication, opting to "wait" for a client to join. If you want more on those two pieces, look back to my last article on deauthentication.
To start with, we'll run iwconfig in our Kali terminal to get the name of our wireless adapter. The name will likely be wlan0, but it could differ.
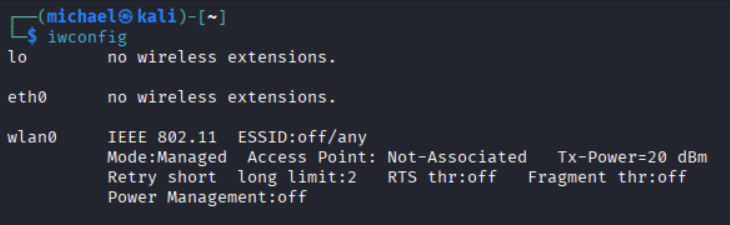
The mode is set to Managed. We need to set it to Monitor. We can do that by using airmon-ng. You may be have conflicting services running that prevent this from happening, like wpa_supplicant. Your terminal will output a suggestion to use sudo airmon-ng check kill to automatically end those specific services.
Remember to run these commands with sudo if not elevated to root.
### Set wlan0 to Monitor
sudo airmon-ng start wlan0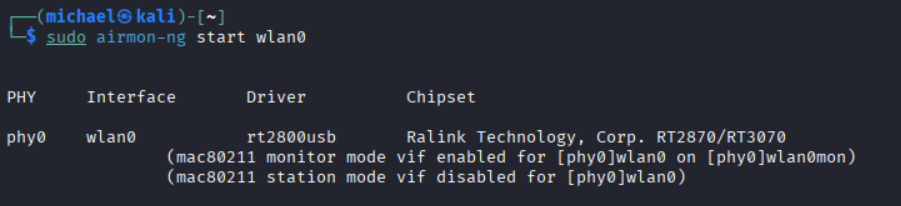
We're ready to monitor for traffic. We'll use airodump-ng to do so. In this scenario, I am going to start my monitor before connecting a client to the LabWiFi network and set our output to save to "labwifi". This will generate several files in our present working directory that begin with "labwifi"; most importantly, the capture (.cap) file. Each filename will be automatically appended with an incrementing two-digit suffix following the declared name.
Monitoring will run and refresh continuously unless exited with Ctrl+C.
### Monitor all traffic associated with the wireless network's MAC address (BSSID), output to pwd
sudo airmon-ng wlan0mon --bssid [wireless network MAC] --channel [channel#] --write [file name]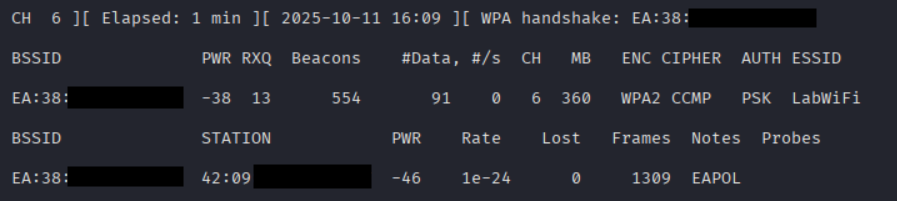
We're almost ready to use our capture file to initiate our dictionary attack. First, we need a dictionary file! Find or create a text file with one string per line. I have a file in my present working directory named "PasswordDump.txt" containing 18 possible passwords. Luckily for me, I own the network and know the password is "P@ssW0rd!P@ssW0rd!". The incorrect passwords before and after are included to show that, given multiple to guess with, we will find the correct one.
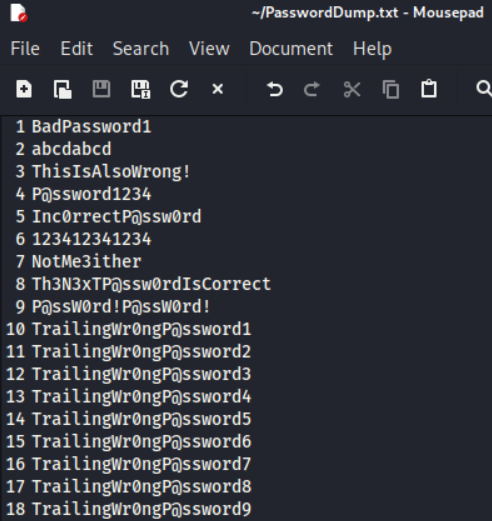
Now we can start guessing passwords. We'll use aircrack-ng along with our capture file and our dictionary file. The aircrack-ng tool will run through the process of hashing and guessing each password in the supplied file, before either giving us "KEY NOT FOUND", meaning none of the supplied values were correct, or "KEY FOUND" along with the correct value.
### Crack the password to the target wireless network using the capture file and dictionary file
sudo aircrack-ng [capture file] -w [dictionary file]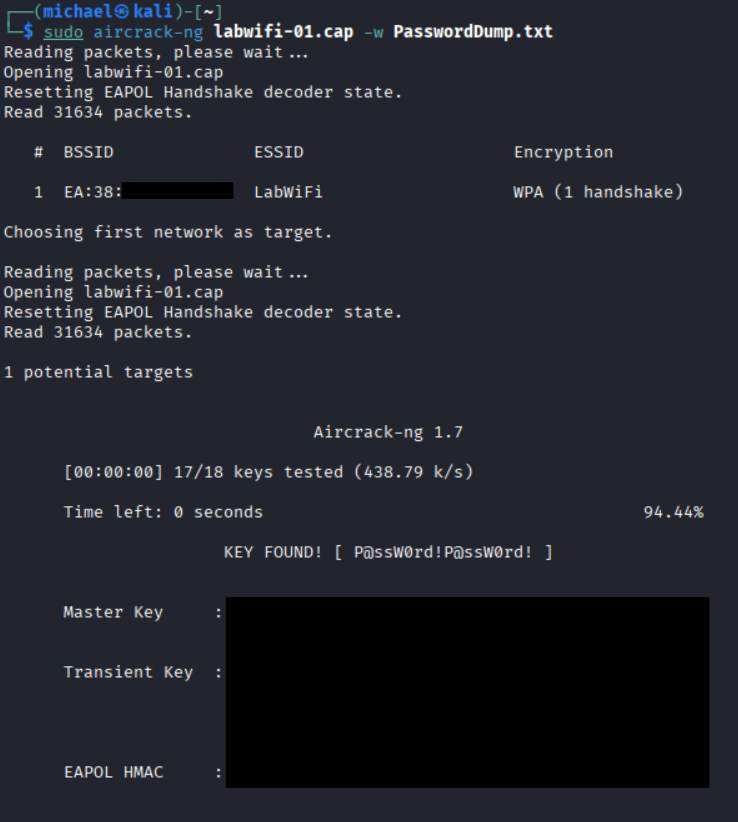
Conclusion
Learning how dictionary attacks work—and seeing them in action—really drives home why strong Wi-Fi security matters. Tools like aircrack-ng are great for teaching and testing, but they also remind us how easy it can be to break into a network with a weak password. Prevention is not only possible - it's often simple. Long and complex passwords and being mindful of the settings you have configured for your wireless network will go a long way.
I encourage everyone with an interest in wireless security to give this and my deauth lab a try. If you do, tell me about your experience! You can reach out to me at any of my linked socials, like my LinkedIn, or email me at [email protected]. In the meantime, check out some of my other Articles. See you all in the next one!